Traffic Conditioners
QoS mechanisms that limit bandwidth are called traffic conditioners and we have already given a quick definition of the two existing types:
Policing typically limits bandwidth by discarding traffic that exceeds a specified rate. However policing also can remark this traffic which is exceeding the specified rate and send the traffic anyway.
Recall also that Policing can be applied on an inbound or outbound direction of an interface.
Shaping as seen before is delaying traffic as it buffers it . The only backdraw is that Shaping can be applied only in the outbound direction of an interface.
So with Policing and Shaping , you can send traffic at an “average” rate which is less that clock rate of your interface. The average bandwidth is called the Commited Information Rate (CIR).
Please note also the following difference between the Shaping and the Policing regarding the Burst.
- The number of bits that is sent during a toming interval is called the Commited Burst ( Bc) => SHAPING
- The number of bytes that is sent during a toming interval is called the Commited Burst ( Bc) => POLICING
The timing interval is written as Tc . So you have the following formulas.
CIR = Bc / Tc
or
Tc = Bc / CIR
If you don’t use your Bc bits or bytes, then you can re-use them for the next timing interval and it is considered as Excess Burst (Be). So Be bits or bytes are the excess packets of Bc that we can send.
Now going more in depth in Cisco technology , we will use the “metaphor” of token bucket for the Bc and Be traffic.
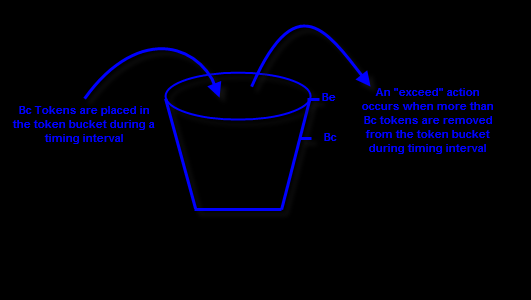
So with policing , traffic that requires no more than the Bc number of bits or bytes to be transmitted is called “conforming traffic” . Traffic that requires more than the Bc numbers of bits or bytes is said to be “exceeding traffic”.
Let’s see the policing approach with a single token bucket approach.
Suppose 500 bytes currently in the token bucket . A packet comes through requiring 300 bytes. The bytes are removed from the bucket and the packet is sent. Then before the bucket has been replenished with more tokens, another 300 bytes packet comes along. Because only 200 bytes remain in the bucket, the packet can’t be sent and is discarded.
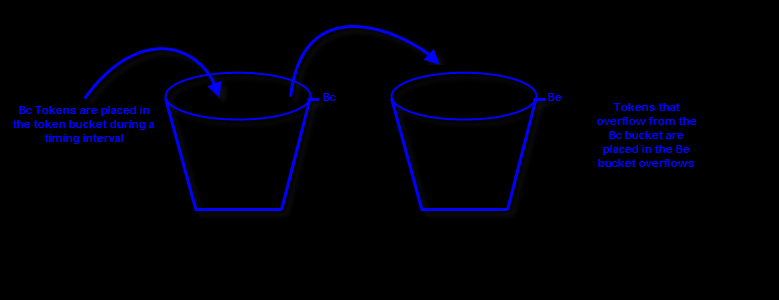
Now let’s continue with an enhancement to the single token bucket approach.
Instead to have one bucket , now a second bucket exists. The first bucket has a depth of Bc and the second bucket has a depth of Be.
If a packet can be forwarded using bytes in the Bc bucket, it is said to be “conforming”. If the packet can’t be forwarded using the bytes in the Bc bucket, but it can be forwarded using the bytes in the Be bucket , it is said to be “exceeding”. If the packet can’t be forwarded using either of the bucket individually , it is said to be “violating”.
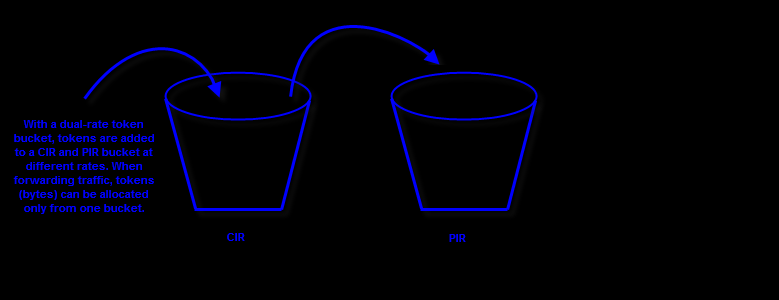
Let’s see the Cisco dual token bucket approach as Cisco also supports dual-rate policing . With dual-rate policing, you still have 2 token buckets. The first bucket is the CIR bucket, and the second bucket is the Peak Information Rate (PIR).
These bucket are replenished with tokens at different rates, with PIR bucket being filled at a faster rate.
When a packet arrives, the dual-rate policer checks to see whether the PIR bucket has enough tokens (that is bytes) to send the packet. If there are not sufficient tokens, the packet is said to be “violating” and it is discarded. Otherwise, the policer checks to see whether the CIR bucket has enough tokens to forward the packet. If the packet can be sent using the CIR bucket’s tokens, the packet is “conforming”. If the CIR bucket’s tokens are not sufficient, but the PIR bucket’s tokens are sufficient then the packet is said to be “exceeding” and an exceed action is applied.
So , you can specify the following various actions to perform based on whether a packet is “conforming”, “exceeding” or “violating”.
- Transmit
- Drop
- Mark
- Multiaction
CB-Shaping Config
One of two approaches can be used when configuring Class-Based Shaping.
- Shaping to Average
- Shaping to Peak
When you configure to shape to an average, you only want to send traffic at the CIR. However, if you configure shaping to peak, you are attempting then to send above the CIR if the bandwidth is available. Specifically, when you shape to peak, instead of just adding Bc bits to the token bucket during each timing interval, you are adding Bc+Be bits to the token bucket. The peak rate is then fiven by the following formula
Peak Rate = CIR * [ 1 + (Be / Bc)]
Recall also that althought shaping to peak can squeeze out some extra bandwidth from a WAN connection, it also can lead to multiple packets drops. !